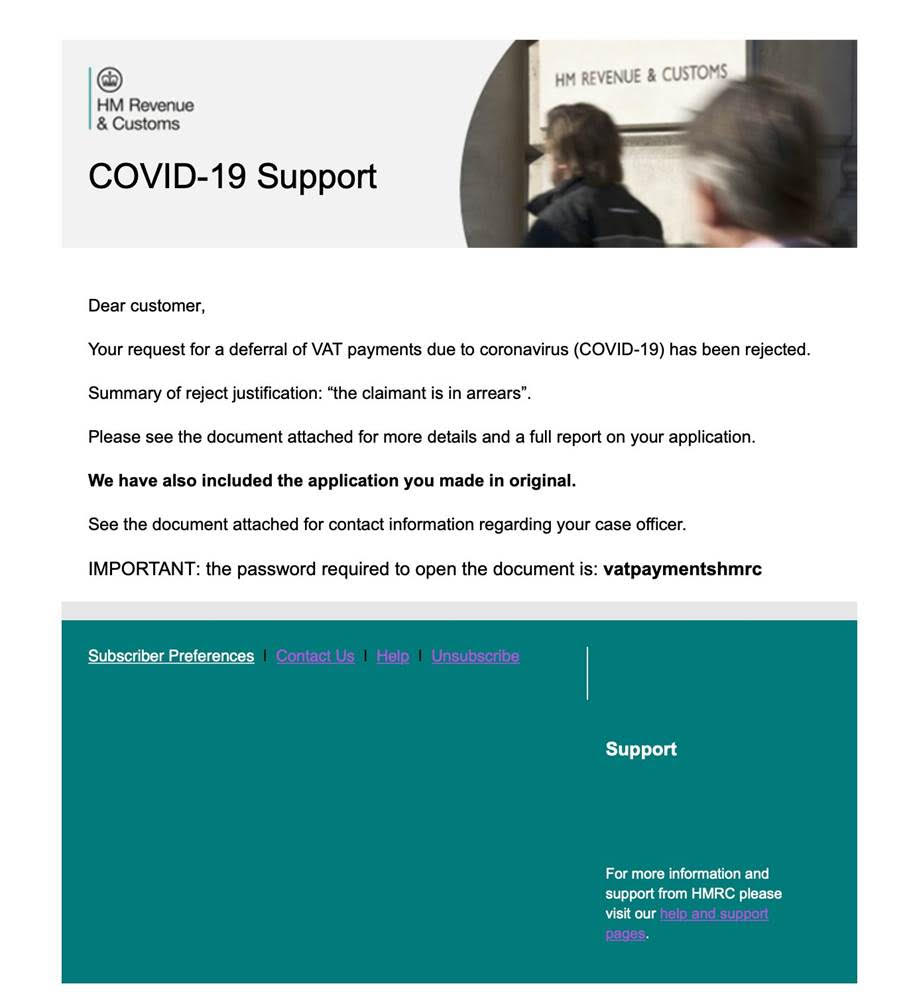
Business owners have been the target of a new email phishing scam purporting to be from HM Revenue & Customs (HMRC).
The scam, which was uncovered by accountancy outsourcing specialists Lanop Outsourcing, uses official HMRC branding and graphics to convince victims that their VAT deferral application has been rejected. At least 100 company owners have reported receiving the realistic scam email through Lanop Outsourcing clients.
To aid struggling businesses during Covid-19, HMRC allowed payments of VAT between March 2020 and June 2020 to be deferred until 31st March 2021. Cyber criminals have used the scheme to trick business owners into revealing sensitive information, such as account names, passwords and payment details.
The phishing email begins: “Dear customers, Your request for a deferral of VAT payments due to coronavirus (COVID-19) has been rejected… Summary of reject justification: ‘the claimant is in arrears.”
The email then attempts to convince the recipient of its legitimacy by attaching a false document with “more details and a full report on your application,” whilst also sharing a one-use password required to open the document and suggesting that the original application has also been reshared.
The victim is then redirected to a false website and prompted to enter certain sensitive information, such as email, passwords and payment details which is then harvested by the hacker.
Cyber security expert Steve Peake, UK Systems Engineer Manager at Barracuda Networks comments: “This phishing attack is the latest in a series of HMRC-branded email scams, designed to trick business owners into handing over confidential data. With many companies struggling due to the disruption caused by the Covid-19 outbreak, we have seen a real uptake in the number of Covid-related attacks targeting business owners and employees. In fact, we recently observed a 667% spike in coronavirus-related spear-phishing attacks from February compared to March, during the start of the UK’s lockdown. Thus, it was only a matter of time before hackers targeted the government’s VAT deferment scheme as a new route to obtaining the bank details of unsuspecting victims.
“Socially engineered service impersonation attacks using trusted brands is unfortunately a growing practice which can be a very successful method of attack, especially when combined with the current world situation. Attackers frequently rely on this form of attack as it delivers an instant level of trust with the email recipient, with many organisations lacking the layered security approach that modern day email security requires.
“Combatting this issue requires business owners and entrepreneurs take email security seriously, ensuing the right systems are in place to highlight and block potentially malicious or suspicious emails before they reach the inbox. It’s also critical that every member of staff is properly trained to spot these scams, especially with so many people still working remotely. For example, HMRC will never ask for credentials of any kind, and it’s important that users understand this as well as other basic security precautions, such as checking the website of any request directly, and never clicking links sent via email.”
Shahzad Ali, Managing Director, Lanop Outsourcing, comments: “This scam is one of the most deceitful and realistic phishing attacks we’ve seen since the start of the Covid-19 pandemic, and its veneer of legitimacy is just strong enough that concerned business owners could easily fall into the trap of handing over personal information.
“In these trying times, a cyber hack should be the least of business owners’ worries, and it’s essential that the source of all significant emails, particularly those purporting to be from a government agency, should be verified before any further action is taken.”